DanaBot Banking Trojan Finds North American Financial Institutions
By: Jim Stickley and Tina Davis
November 8, 2018
Traditionally, when we discuss the DanaBot banking Trojan, we’re primarily talking about it targeting financial institutions in Australia and Europe. Now, it’s making its way to targets within the United States. Discovered by ProofPoint, it spreads through spam with malware pretending to be from eFax. Ignoring the fact that fewer and fewer use faxing these days, any communication that you are not expecting should be scrutinized thoroughly.

This evolution of what researchers think is a form of CryptXXX ransomware targets Wells Fargo and Bank of America in North America, but no financial institution is safe from similar attacks. The original message is a well-done one appearing to come from eFax. The sender’s address is even faked to make it appear that eFax was the domain it hailed from. But don’t be fooled. If either the link or the “Download Fax” button is clicked, a Microsoft Word document appears that sets off a macro sequence, which is actually getting a downloader on to the computer that subsequently downloads DanaBot and other malware.
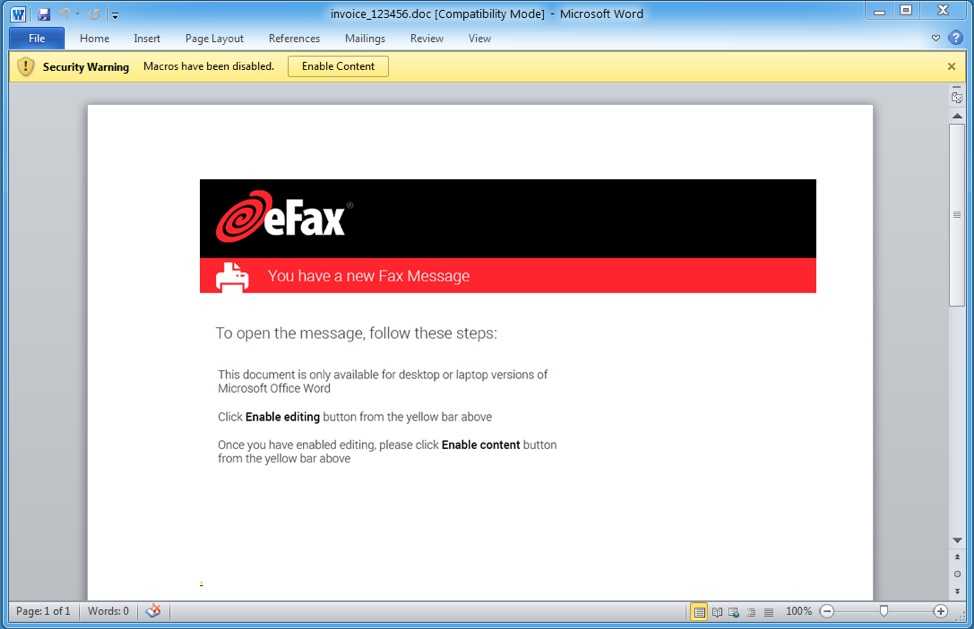
Always use extreme caution when clicking links or clicking buttons in an email message. The same goes for clicking on attachments. No type of attachment is safe these days. Malware has been found in .doc, .exe, .pdf, .img, .mpg and about any other extension you can think of. If you’re not  expecting something, just delete it. If you are not sure that you should just toss in File 13, contact the sender by placing a call to a phone number you already know is safe or by paying a personal visit to his or her desk.
expecting something, just delete it. If you are not sure that you should just toss in File 13, contact the sender by placing a call to a phone number you already know is safe or by paying a personal visit to his or her desk.
DanaBot can steal login credentials, log keystrokes, or take screenshots, among other devious acts. Always keep antivirus software loaded and updated on all devices and be sure to apply updates and patches as soon as they are made available to you.
ProofPoint researchers believe that DanaBot is being used among a group of affiliates who share profits or merely rent the malware, netting the developer a handsome chunk of change.